Devs
Understand, Strengthen and Prove Your Device’s Security and Privacy
EDAMAME Security is your all-in-one tool to secure, understand and prove your dev workstation—from OS to network. It delivers compliance audits, network analysis, and vulnerability insights, all while seamlessly integrating with your workflows and OS.
Manifesto
Our Manifesto for Developers: You are the future of SDLC Security
At EDAMAME, we believe that developers are the cornerstone of SDLC Endpoint Security. Our goal is to empower you to build secure, resilient software without compromising your creativity or productivity.
Features
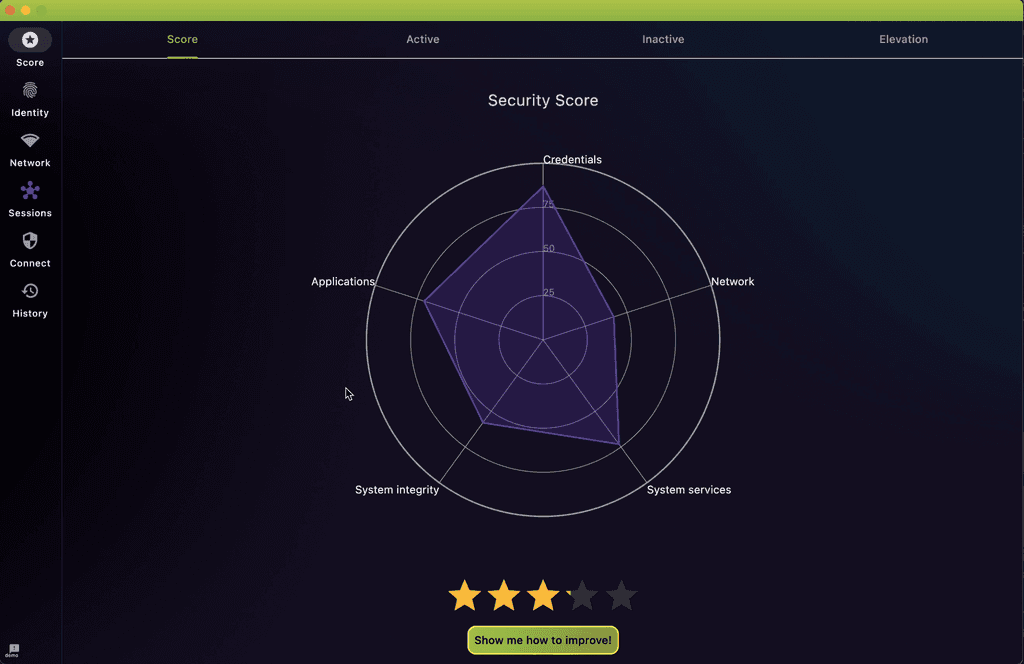
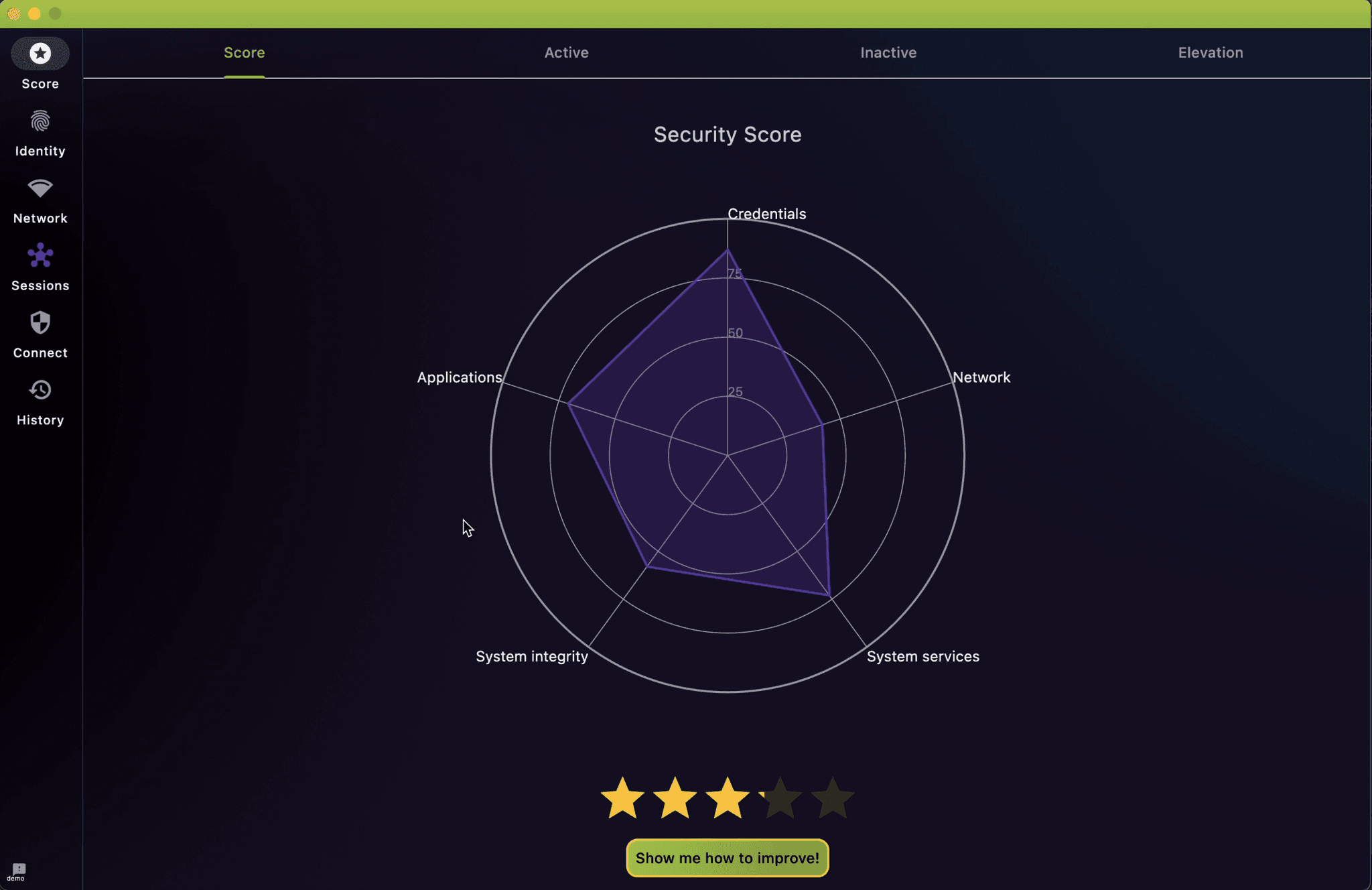
Transform Your Security Workflow
Grasp your laptop or tablet's security status and become an active contributor to your cyber protection. EDAMAME Security not only offers insights but also steers you toward automated modifications to lessen potential dangers. Equip yourself with the understanding and skills required to safeguard your equipment against digital risks, elevating your security stance to meet the most rigorous corporate norms—all while ensuring your privacy remains intact.
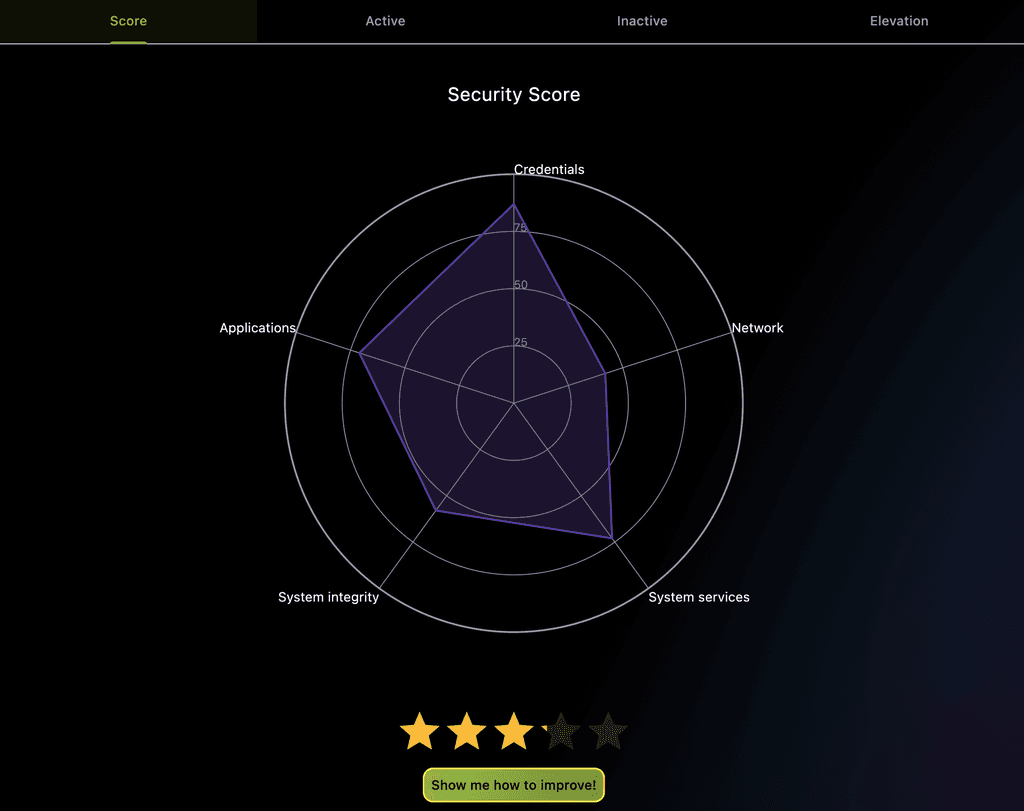
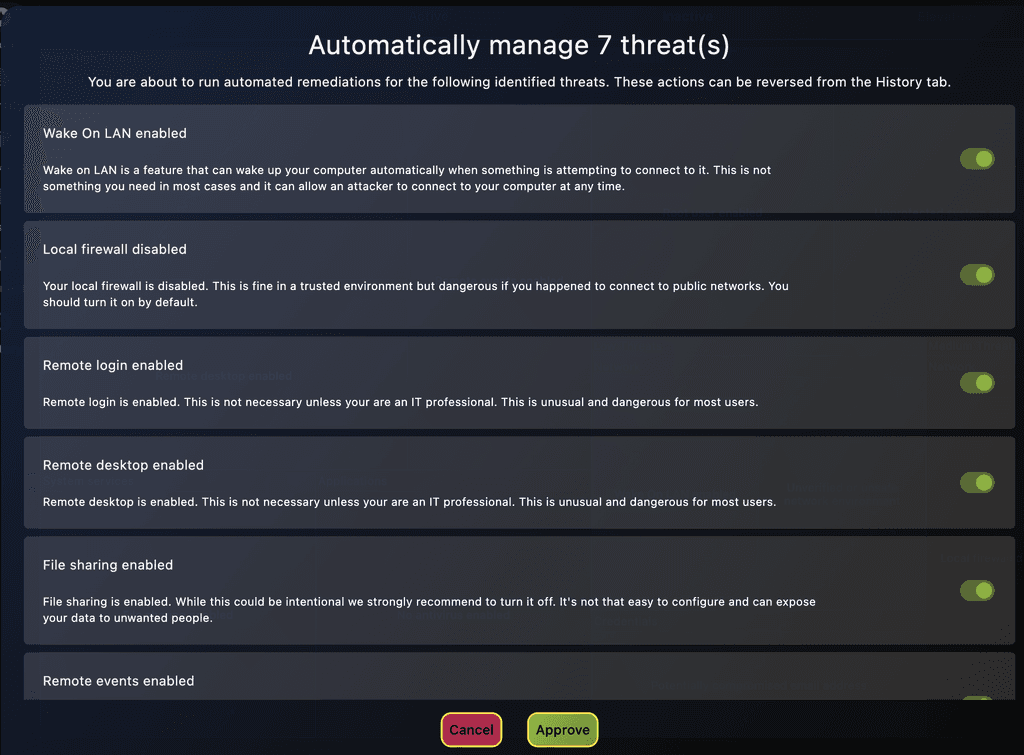
Automated Audits and Hardening
Quickly assess your system's security alignment with beast practices. Get guidance and perform changes automatically.
Produce Signed Compliance Reports
Make your endpoint ISO27001/SOC2-compliant and generate signed compliance reports.
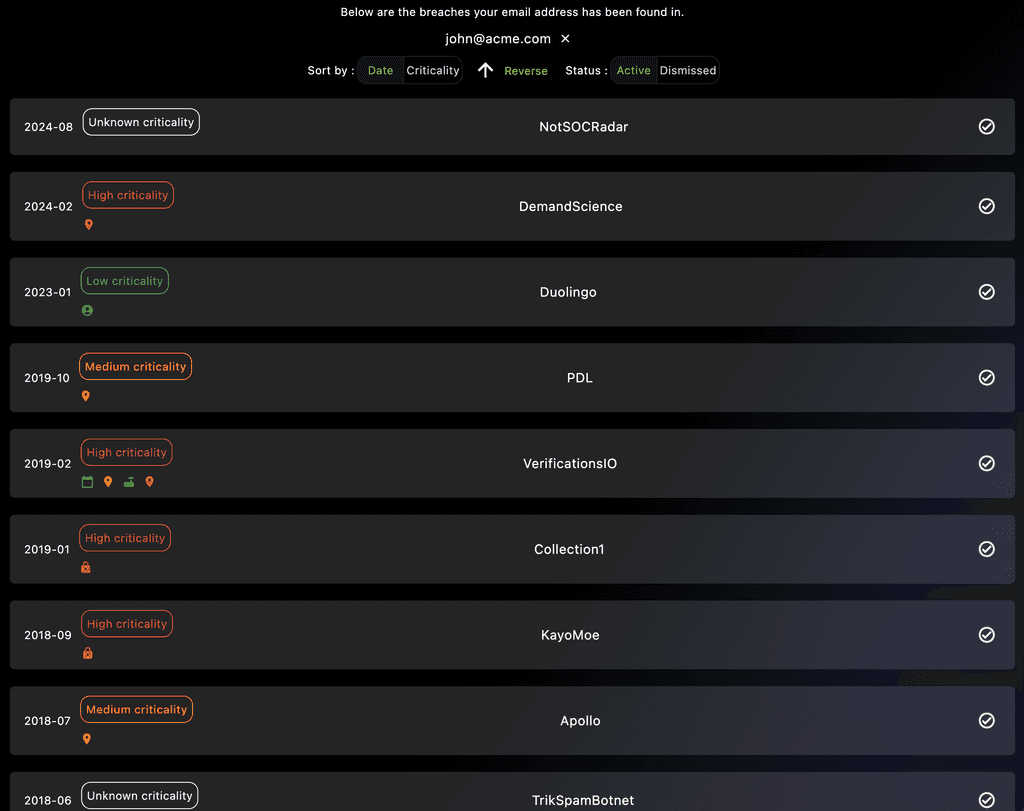
AI-Enhanced Identity Breach Management
Verify if your credentials have been compromised and receive AI-driven assistance. Stay proactive with insights into data breaches affecting your email addresses.
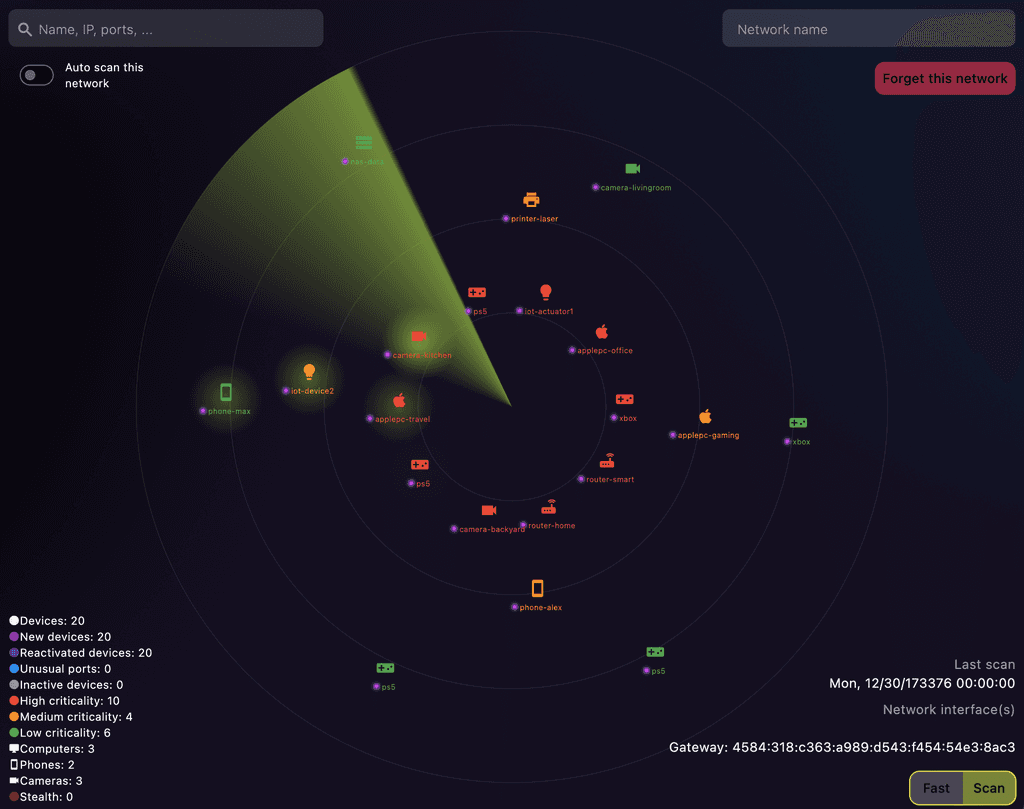
Advanced Network Scanning with AI Analysis
Discover all devices on your local network and evaluate risks using AI technology. Highlight vulnerabilities and fortify your network with NMAP-inspired scanning.
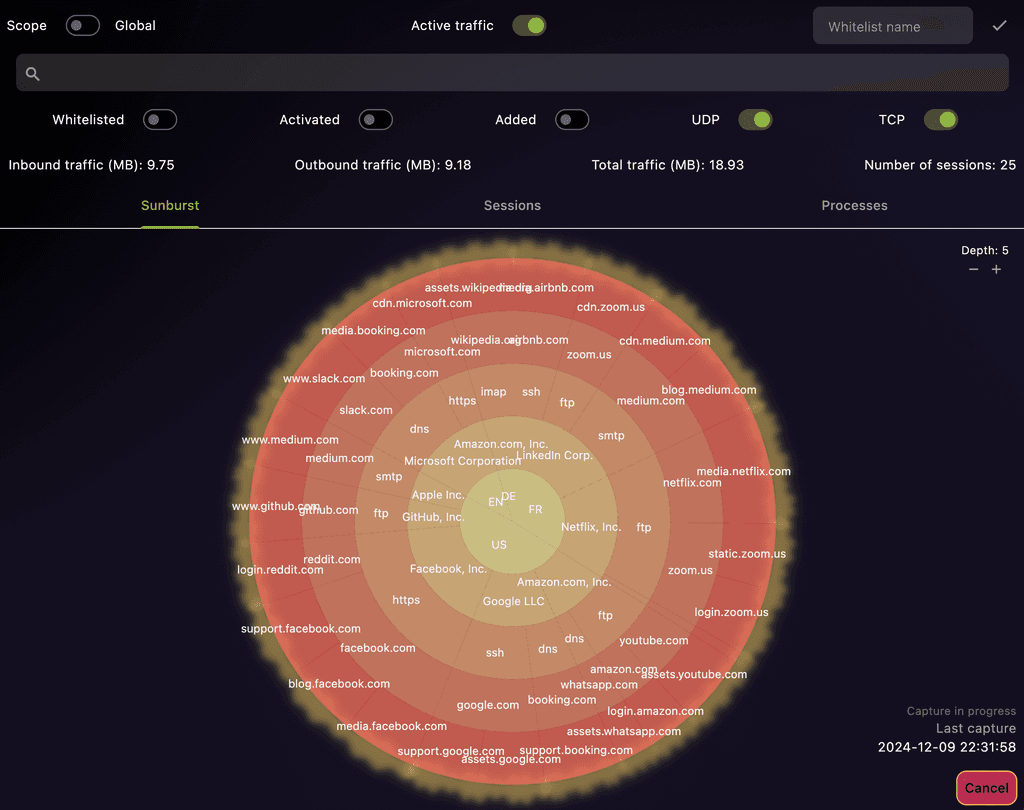
Process-Level Network Traffic Analysis
Visualize your machine’s inbound and outbound traffic with process-level and domain name details. Easily identify which processes communicate with which domains.
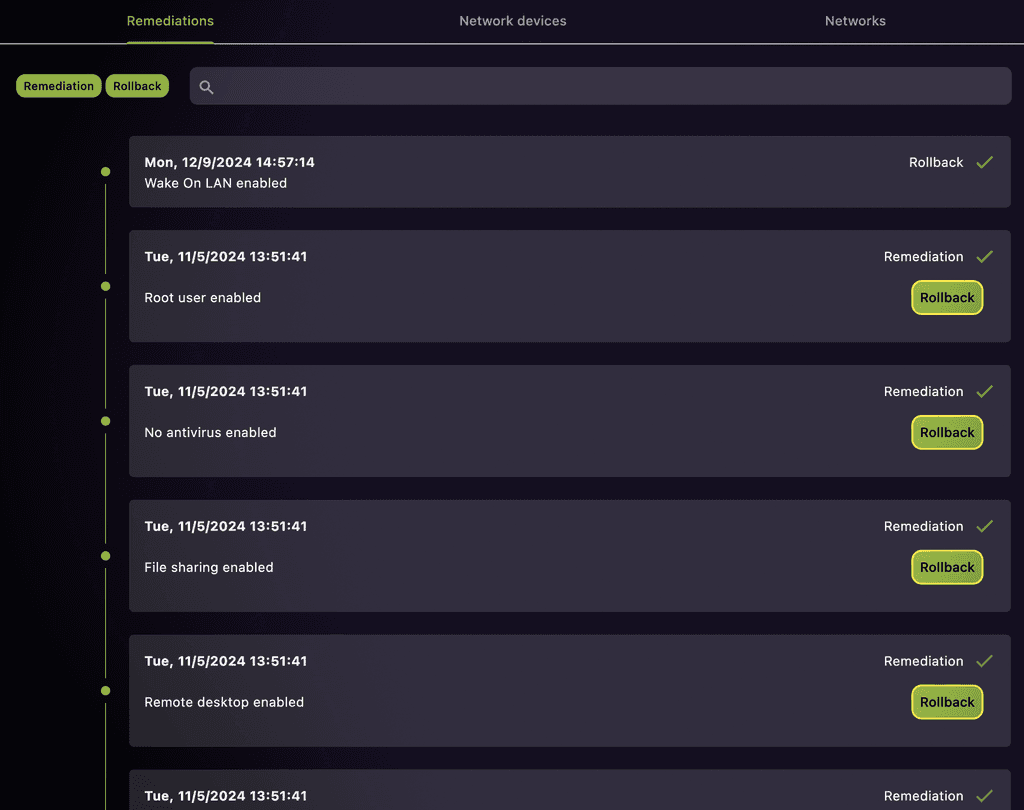
History and Rollback
Easily track changes made to your system's security settings and roll back modifications if needed. Maintain control over your configurations with a comprehensive history log.
Who?
Who Is EDAMAME Security For?
Reap the advantages of Centralised Endpoint Management for any device, whether company-held, owned by contractors or personal use, while simultaneously enforcing security, privacy, and confidentiality.
Testimonials
As developers ourselves, we intimately understand the challenges of balancing security with productivity. These testimonials reaffirm our developer-first mission—to create tools that empower innovation while seamlessly enhancing security.