Back
Nov 22, 2024
Achieving SOC2 Compliance Across the Software Development Life Cycle without MDM/UEM

Frank Lyonnet

In today’s fast-paced software development environments, safeguarding critical assets such as code, secrets, and test data is paramount. For organizations aiming to achieve SOC 2 compliance, ensuring the protection of these assets aligns with the Trust Services Criteria (TSC) established by the American Institute of Certified Public Accountants (AICPA). This blog post delves into how various components of the SDLC—company-owned machines, contractor devices, and Continuous Integration/Continuous Deployment (CI/CD) environments—can be effectively secured to meet SOC 2 standards without relying on traditional Mobile Device Management (MDM) or Unified Endpoint Management (UEM) solutions. We will introduce EDAMAME, our innovative solution, and demonstrate how it addresses mandatory SOC 2 requirements to secure all devices, irrespective of their access criticality.
Understanding Critical Assets in the SDLC
SOC 2 compliance revolves around the Trust Services Criteria, which include Security, Availability, Processing Integrity, Confidentiality, and Privacy. Within the SDLC, critical assets must be protected to uphold these criteria. Proper classification and protection of these assets are essential for maintaining the integrity and confidentiality required by SOC 2.
1. Code
Criticality: Code is the backbone of any software product, often containing proprietary algorithms and intellectual property. Unauthorized access or leaks can result in competitive disadvantages or introduce security vulnerabilities.
Access Points: Developer machines, code repositories, and CI/CD systems.
2. Secrets
Criticality: Secrets encompass passwords, API keys, certificates, and other credentials. Their compromise can lead to unauthorized system access and data breaches. While some secrets are critical, others may have limited impact depending on their usage.
Access Points: Developer environments, CI/CD pipelines, and configuration files.
3. Test Data
Criticality: Test data may include sensitive information such as customer or patient data, particularly in regulated industries like healthcare. Protecting this data is crucial under regulations such as the Health Insurance Portability and Accountability Act (HIPAA) in the US, the General Data Protection Regulation (GDPR) in the EU, and the California Consumer Privacy Act (CCPA).
Access Points: Testing environments, developer machines, and CI/CD systems.
Understanding Endpoints in the SDLC
Developer Machines
Developer machines are utilized by software engineers to write, test, and debug code. These machines can be categorized as:
Corporate Devices: Owned and managed by the organization.
Personal Devices: Owned by employees (Bring Your Own Device - BYOD).
Contractor Devices: Owned by third-party contractors collaborating with the organization.
CI/CD Runners
CI/CD runners are servers or virtual machines that automate tasks in the software delivery pipeline, such as building code, running tests, and deploying applications. These can be:
Self-Hosted Runners: Hosted within the organization's infrastructure (cloud or on-premises).
Cloud-Based Runners: Provided by cloud services like GitHub Actions or GitLab CI/CD.
How Endpoints Interact with Critical Assets
Development and Testing
Data Access: Developers and CI/CD systems require access to critical test data for validation and testing purposes.
Code Repositories: Source code is pulled to developer machines or CI/CD systems for modification, compilation, or testing.
Secrets Management: Secrets are retrieved from secure storage into developer machines or CI/CD systems as needed for testing or building.
All SDLC components—corporate machines, contractor devices, and CI/CD environments—must be secured to protect access to critical data, aligning with SOC 2’s Security and Confidentiality criteria.
Mandatory Controls for SOC 2 Compliance
To achieve SOC 2 compliance, organizations must implement controls that align with the Trust Services Criteria. Below are essential controls that should be applied to all endpoints, regardless of ownership:
1. Access Control
Least Privilege Principle
Requirement: Users should have the minimum access necessary to perform their roles.
Implementation: Assign roles and permissions meticulously, ensuring users only access what they need.
SOC 2 Alignment: Security Principle – Logical and Physical Access Controls.
Multi-Factor Authentication (MFA)
Requirement: MFA must be enforced for accessing systems handling critical assets.
Implementation: Deploy MFA solutions compatible with all device types to add an extra layer of security.
SOC 2 Alignment: Security Principle – Authentication Mechanisms.
2. Encryption
Data at Rest
Requirement: Encrypt critical assets stored on devices to protect against unauthorized access.
Implementation: Utilize full-disk encryption tools such as AES-256.
SOC 2 Alignment: Security Principle – Data Encryption.
Data in Transit
Requirement: Secure data transmission channels to prevent interception and tampering.
Implementation: Implement HTTPS, SSH, and VPNs for all data transfers.
SOC 2 Alignment: Security Principle – Network Security.
3. Endpoint Protection
Antivirus and Anti-Malware
Requirement: Protect all endpoints against malicious software.
Implementation: Install and regularly update security software to detect and mitigate threats.
SOC 2 Alignment: Security Principle – Malware Protection.
Firewall Configurations
Requirement: Control network traffic to and from devices.
Implementation: Enable and configure firewalls on all devices to restrict unauthorized access.
SOC 2 Alignment: Security Principle – Network Security.
Regular Updates and Patch Management
Requirement: Keep all systems up to date with the latest security patches.
Implementation: Enforce update policies across devices to address vulnerabilities promptly.
SOC 2 Alignment: Security Principle – System Maintenance.
4. Monitoring and Logging
Audit Logs
Requirement: Record access and activities on all critical assets.
Implementation: Deploy logging solutions that operate across different devices to maintain comprehensive audit trails.
SOC 2 Alignment: Security Principle – Event Logging.
5. Secure Configuration
System Hardening
Requirement: Disable unnecessary services and configure systems securely.
Implementation: Apply configuration standards such as CIS Benchmarks to minimize attack surfaces.
SOC 2 Alignment: Security Principle – System Configuration.
Configuration Management
Requirement: Maintain secure configurations consistently across all devices.
Implementation: Use configuration management tools to enforce and monitor settings.
SOC 2 Alignment: Security Principle – Configuration Management.
Why Traditional MDM/UEM Approaches Fall Short for SOC 2 in the SDLC
Traditionally, organizations have relied on Admin-Down approaches through Mobile Device Management (MDM) and Unified Endpoint Management (UEM) systems to implement necessary security measures for SOC 2 compliance. However, these solutions present several challenges:
1. High Administrative Burden
Resource Intensive: Managing, monitoring, and enforcing security policies across every device demands significant time and resources, straining IT teams and budgets.
2. User Resistance
Perceived Restrictions: Strict administrative controls can lead to user frustration and decreased morale.
Potential Workarounds: Users may attempt to bypass security measures, inadvertently creating vulnerabilities.
3. Incompatibility with Contractor Devices
Legal and Privacy Issues: Enforcing administrative controls on non-corporate devices can lead to privacy concerns and legal complications, especially with contractor-owned hardware.
4. Limited Flexibility for Developers
Restricted Access: Developers often need elevated privileges for tasks like installing software or accessing specific system resources. Admin-Down tools may hinder productivity.
Bypassing Controls: Rigidity can prompt developers to disable MDM/UEM controls, compromising security.
5. Scalability Challenges
Operational Costs: Scaling Admin-Down solutions to accommodate growing numbers of devices and users is complex and costly.
Maintenance Overhead: Continuous updates and policy enforcement across an expanding device base can overwhelm IT teams.
Introducing EDAMAME: A User-Up Approach for SOC 2 Compliance
EDAMAME offers a revolutionary alternative to traditional MDM/UEM solutions by adopting a User-Up approach. Designed to empower users while ensuring SOC 2 compliance, EDAMAME shifts the responsibility of security to the users in a supportive and guided manner. This approach overcomes the limitations of Admin-Down strategies without relying on invasive device management tools.
Key Features of EDAMAME
User Empowerment
Functionality: Users install the EDAMAME application on their devices, which guides them through implementing required security controls, such as enabling encryption or updating antivirus software.
Benefit: Ensures appropriate application of security measures without imposing unnecessary restrictions.
Continuous Compliance Verification
Functionality: The EDAMAME application continuously verifies device compliance with the organization’s security policies aligned with SOC 2 criteria.
Benefit: Maintains device security over time, adapting to new threats and compliance requirements proactively.
Access Control Integration
Functionality: If a device becomes non-compliant, EDAMAME integrates with access control systems to automatically restrict access to critical assets until compliance is restored.
Benefit: Minimizes security risks by ensuring only compliant devices can access sensitive data.
Privacy-Preserving
Functionality: EDAMAME collects only essential information required to verify compliance, respecting user privacy.
Benefit: Ideal for both personal and contractor-owned devices, ensuring seamless integration without intrusive data access.
Applying SOC 2 Controls Across All SDLC Endpoints with EDAMAME
EDAMAME effectively applies SOC 2 controls across all endpoints involved in the SDLC, ensuring comprehensive compliance and security.
1. Access Control Enhancement
User Responsibility: Users ensure their devices meet access control requirements, such as enabling MFA and adhering to the least privilege principle.
Dynamic Access Management: EDAMAME integrates with authentication systems to grant or revoke access based on real-time compliance status.
2. Encryption Enforcement
Guided Implementation: The EDAMAME client assists users in enabling full-disk encryption and securing data in transit.
Compliance Verification: Continuously verifies that encryption standards are maintained on the device.
3. Endpoint Protection
User-Led Updates: Users are prompted to install antivirus software, enable firewalls, and apply security patches.
Automated Compliance Checks: EDAMAME monitors these protections and informs users of any required actions.
4. Monitoring and Logging
Transparent Logging: EDAMAME collects compliance status without intrusive monitoring, respecting user privacy.
Centralized Reporting: Administrators receive compliance reports, enabling them to demonstrate adherence to SOC 2 requirements without managing individual devices.
5. Secure Configuration Management
User Guidance: Provides instructions for system hardening and secure configurations.
Compliance Assurance: Ensures that devices adhere to the organization’s security policies through user participation.
Benefits of the User-Up Approach with EDAMAME
Adopting EDAMAME's User-Up approach offers numerous advantages over traditional Admin-Down methods, aligning perfectly with SOC 2’s Trust Services Criteria.
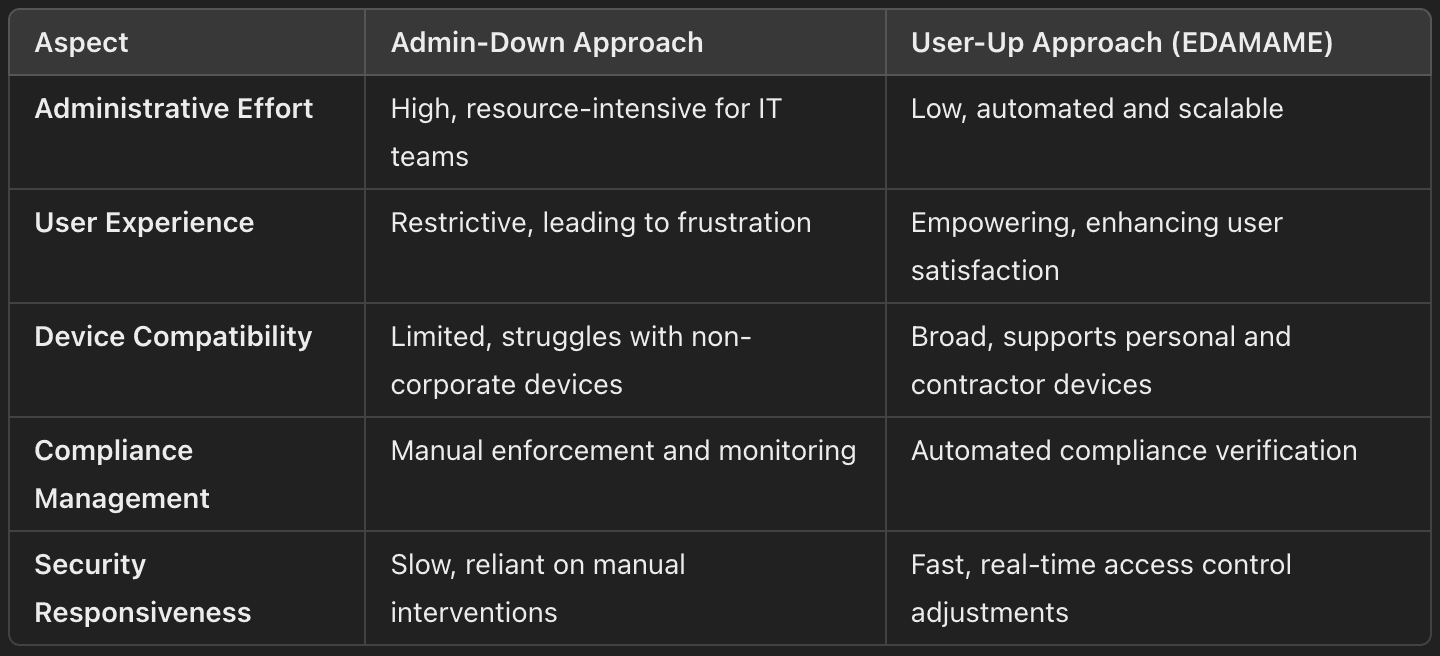
Reduced Administrative Overhead
Efficiency: Administrators no longer need to manually push updates or enforce policies across diverse devices.
Scalability: The User-Up model scales effortlessly, accommodating growth in users or devices without added complexity.
Enhanced User Engagement and Responsibility
Ownership: Users take an active role in maintaining their device security, leading to better adherence to policies.
Awareness: Increased user involvement fosters a culture of security awareness within the organization.
Compatibility with Contractor Devices
Privacy Respect: Contractors can use their own devices without intrusive administrative controls, as EDAMAME ensures compliance without accessing personal data.
Ease of Onboarding: Quickly integrate contractors into the secure environment without complex device management procedures.
Minimized User Frustration
Autonomy: Users retain control over their devices, reducing frustration associated with restrictive administrative controls.
Seamless Workflow: EDAMAME operates unobtrusively, ensuring security measures do not impede productivity.
Immediate Security Response
Real-Time Enforcement: Access to critical assets is automatically restricted if a device falls out of compliance, promptly mitigating security risks.
Dynamic Compliance: Access is restored as soon as users rectify compliance issues on their devices, minimizing downtime.
How to Implement EDAMAME: A Simple Guide
Implementing EDAMAME into your organization’s SDLC is straightforward and designed to integrate seamlessly with existing workflows. Follow these steps to enhance your security and achieve SOC 2 compliance effortlessly:
1. Download the EDAMAME Application
Visit the relevant app store for your developers’ devices—whether it's the Microsoft Store, App Store, Snap Store, Mac App Store, or Google Play—and download the EDAMAME Security application. This app secures developer workstations and contractor devices without disrupting daily workflows.
2. Install and Configure
Install the EDAMAME application on all relevant devices, ensuring compatibility across Windows, macOS, Linux, iOS, and Android platforms. The installation process is lightweight and non-intrusive, allowing developers to retain necessary administrative rights while maintaining security.
3. Utilize the Open Source Helper for System Remediation
Leverage our open-source helper tools available on GitHub to assist with system remediation. These tools empower developers to actively address vulnerabilities and enhance system security without extensive manual intervention.
4. Integrate EDAMAME into Your CI/CD
Check our GitHub repository and install the edamame_posture CLI command for Windows, Linux, and macOS, designed to harden and ensure safe access to code and secrets from any machines, including test machines and CI/CD runners. Utilize the GitHub/GitLab wrappers for easy setup.
5. Monitor and Maintain
Use the EDAMAME Hub for continuous monitoring and logging of your security posture across the entire SDLC. Regularly review dashboards and alerts to stay ahead of potential threats and maintain compliance with SOC 2 standards. This ongoing maintenance ensures that security evolves alongside your development processes.
EDAMAME is designed to be easy to integrate into your development workflow:
Free to Try: Experience the benefits of EDAMAME without upfront costs.
Self-Service Onboarding: Quickly and seamlessly integrate EDAMAME through our portal at hub.edamame.tech.
Open Source Tools: Explore tools at github.com/edamametechnologies.
Conclusion
Achieving SOC 2 compliance across all devices involved in the SDLC is essential yet challenging. Traditional Admin-Down approaches often fall short due to high administrative overhead, user frustration, and incompatibility with non-corporate devices.
EDAMAME Technologies provides a User-Up solution that empowers users to take an active role in maintaining compliance. By ensuring that devices meet security controls and integrating with access control systems to restrict access when necessary, EDAMAME effectively balances security with productivity. This approach not only reduces administrative workload but also enhances user satisfaction and is compatible with contractor devices.
In an era where cyber threats are increasingly sophisticated and regulatory landscapes are ever-evolving, organizations cannot afford to leave any endpoint unsecured. Implementing a solution like EDAMAME, which leverages user responsibility and automated access control, is a strategic move toward robust security and SOC 2 compliance. By adopting this User-Up approach, organizations can confidently navigate the complexities of SOC 2 compliance, protect their critical assets, and foster an environment where security and productivity coexist seamlessly.
Frank Lyonnet
Share this post